Deep Web and Dark Web
In this age of high web technology, the usage of the web has increased tremendously. Thus search engines are on their ways to update their existing algorithms along with...
In this age of high web technology, the usage of the web has increased tremendously. Thus search engines are on their ways to update their existing algorithms along with...

If you think KRACK attack for WiFi is the worst vulnerability of this year, then hold on… …we have got another one for you which is even worse. Microsoft, Google, Lenovo,...
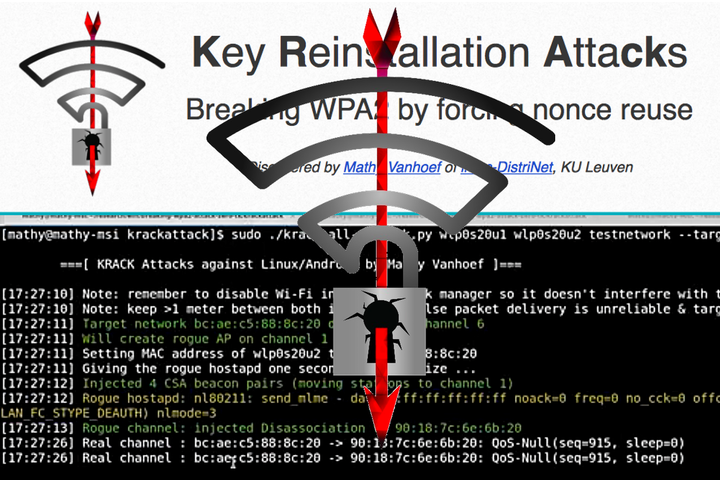
When a vulnerability that can compromise the security of anyone using a Wi-Fi connection, IT pros tend to take notice. In case you slept in late this Monday, here’s...

Armis Labs revealed a new attack vector endangering major mobile, desktop, and IoT operating systems, including Android, iOS, Windows, and Linux, and the devices using them. The new vector...

Hardly a few months back, multinational organizations were hit by WannaCry Ransomware. Currently a new ransomware called Petya has attacked prominent organizations. Ukraine PCs were first hacked by this...